Don’t know where to start running AIX or IBM i workloads in the cloud? IBM Power Systems Virtual Servers in IBM Cloud provide significant value as an addition to your on-premises IBM Power Systems environment. Read this blog to get four tips for a smooth start with this new technology. Read More…
Monthly Archives: August 2020
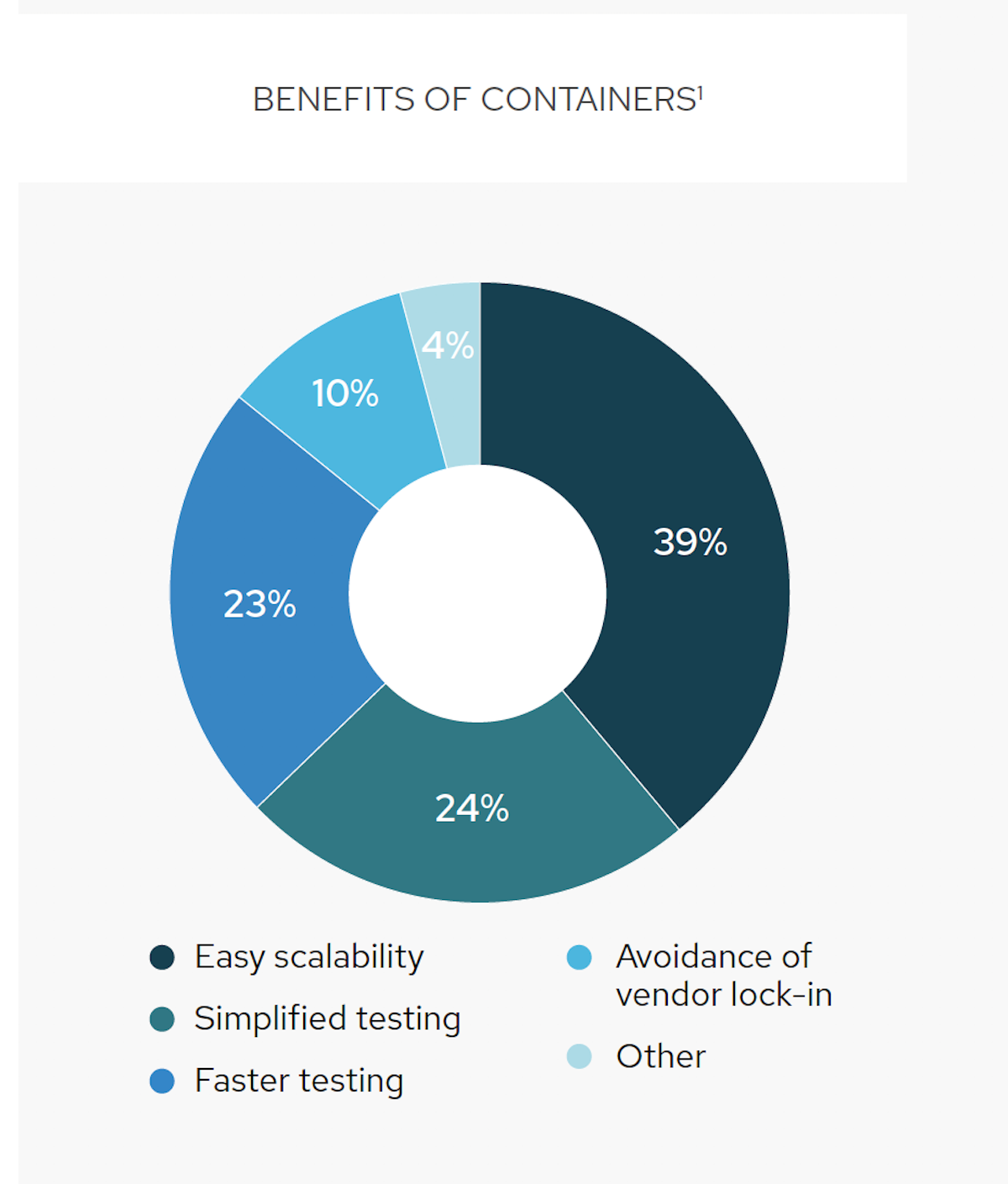
Embracing Containers
This solution brief educates readers on what containers are, why IT leaders should use them and why Red Hat OpenShift for hybrid and multicloud deployments is the game changer in container technology. View: Embracing Containers
Boost business agility
This eBook guides businesses on their journey to boost business agility and gives tips on modernizing IT with hybrid cloud and containers. View: Boost business agility
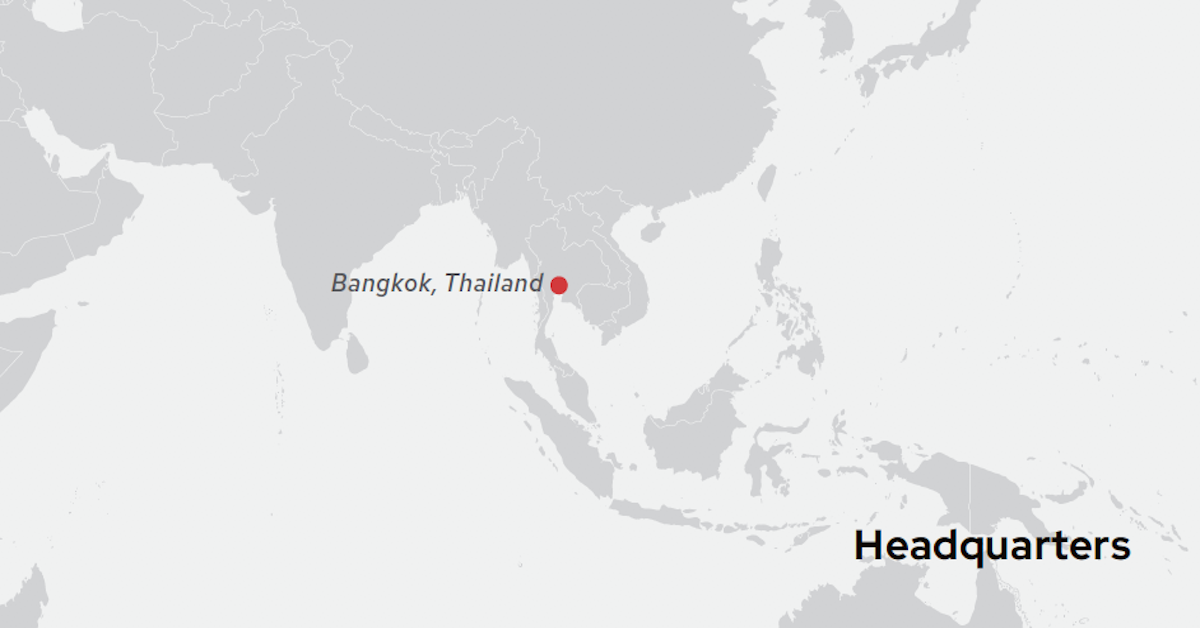
Thai Bank Speeds & Scales Services
This customer success story details how Kasikorn Business-Technology Group (KBTG) turned to Red Hat to update and optimize IT infrastructure and super charge its mobile banking app to handle massive transaction volumes. View: Thai Bank Speeds & Scales Services
Global State of Least Privilege Cyber Security
More than 80% of breaches involve user credentials. Once a cybercriminal is in, they can move around undetected. The 2020 Global State of Least Privilege Cyber Security report provides a look at how businesses are handling privileged access, offers takeaways on how to improve your least privilege efforts. View: Global State of Least Privilege Cyber …
Continue reading “Global State of Least Privilege Cyber Security”
The ABCs of Mobile Device Management
This eBook gives a fun and informative overview of challenges and priorities to tackle when managing mobile devices in your organization. View: The ABCs of Mobile Device Management
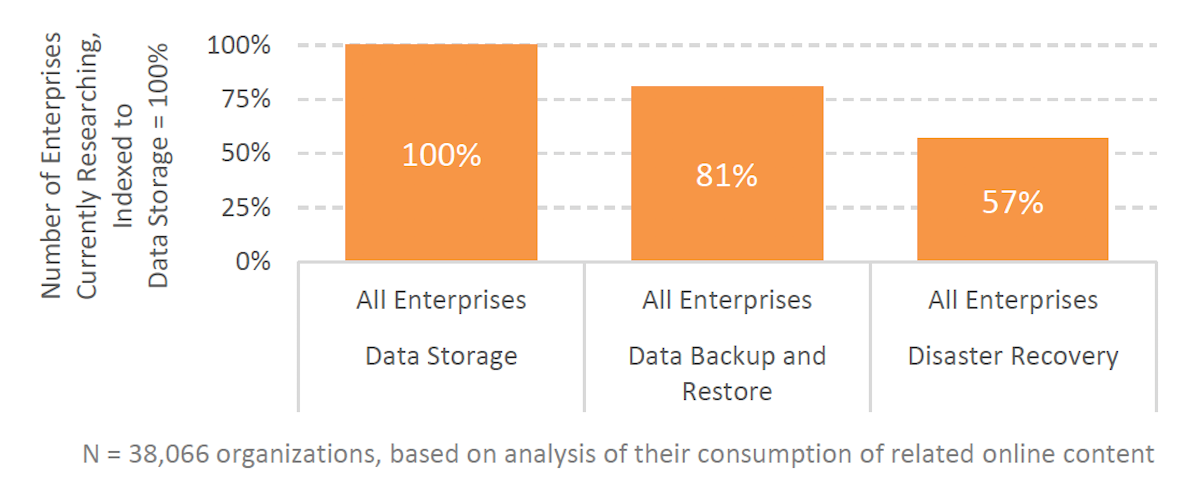
Quantifying how disaster recovery in the cloud reduces risk
Fast and reliable time-to-recover after unplanned downtime is key to reducing your risks. Download this Aberdeen report to understand how to quantify the business value of disaster recovery and the advantages of cloud solutions. View: Quantifying how disaster recovery in the cloud reduces risk
7 Security Areas to Focus on During COVID-19
Rapid response to the coronavirus pandemic means organizations are vulnerable to security breaches due to widespread work-at-home arrangements. Security and risk teams must remain vigilant and focus on new strategic areas. This article from Gartner offers seven focus areas for security leaders in order to ensure work continues securely – even if it is off …
Continue reading “7 Security Areas to Focus on During COVID-19”
Boost business agility
In a world where users demand new applications, features, and updates across all their devices in real time, container technology is critical. This e-book offers insight into how containers let developers work smarter by creating consistent environments to rapidly develop and deliver cloud-native applications that can run anywhere. We recommend both posting the eBook on …
The CISO Challenge: Aligning Business Enablement with Enforcement
New research from Thycotic finds executive board perceptions restrict cyber security effectiveness. Use this informative report to bring focus to the challenges security leaders face when it comes to getting executive buy-in on security initiatives and policies. View: The CISO Challenge: Aligning Business Enablement with Enforcement